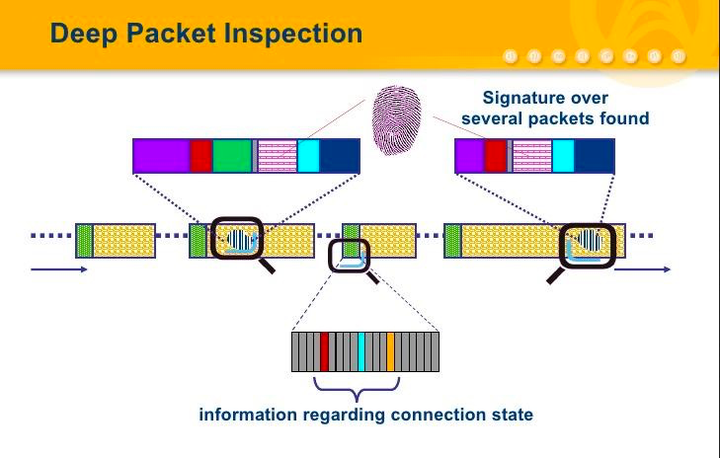
Inspectio Profunda Fasciculorum (DPI)Ars est quae in Intermediariis Fasciculorum Retiariorum (NPBs) adhibita est ad contenta fasciculorum retiariorum in gradu granulari inspicienda et analysanda. Implicat examinationem oneris, inscriptionum, et aliarum informationum protocollo-propriarum intra fasciculos ad perspicientiam accuratam in negotiationem retiariam acquirendam.
DPI ultra simplicem analysin inscriptionum progreditur et profundam comprehensionem datorum per rete fluentium praebet. Permittit inspectionem accuratam protocollorum strati applicationis, ut HTTP, FTP, SMTP, VoIP, vel protocollorum transmissionis imaginum. Examinando ipsum contentum intra fasciculos, DPI potest applicationes specificas, protocolla, vel etiam exempla datorum specifica detegere et identificare.
Praeter analysin hierarchicam inscriptionum fontium, inscriptionum destinationum, portuum fontium, portuum destinationum, et generum protocollorum, DPI etiam analysin strati applicationis addit ad varias applicationes et contenta earum identificanda. Cum data fasciculi 1P, TCP vel UDP per systema administrationis latitudinis transmissionis innixum technologiae DPI fluunt, systema contenta oneris fasciculi 1P legit ad informationem strati applicationis in protocollo OSI Strati 7 reorganizandam, ita ut contenta totius programmatis applicationis obtineat, deinde negotiationem secundum rationem administrationis a systemate definitam formet.
Quomodo DPI operatur?
Muri ignis traditionales saepe carent vi computandi ad perficiendas diligentes inspectiones in tempore reali in magnis voluminibus negotiationis. Progrediente technologia, DPI adhiberi potest ad perficiendas inspectiones complexiores ad inspiciendas capita et data. Typice, muri ignis cum systematibus detectionis intrusionum saepe DPI utuntur. In mundo ubi informatio digitalis maximi momenti est, omnis pars informationis digitalis per interrete in fasciculis parvis traditur. Hoc includit epistulas electronicas, nuntios per applicationem missus, situs interretiales visitatos, sermones per imagines moventes, et plura. Praeter data ipsa, hi fasciculi metadata includunt quae fontem negotiationis, contentum, destinationem, et alias informationes importantes identificant. Cum technologia filtrationis fasciculorum, data continenter monitorari et administrari possunt ut certi sint ea ad locum rectum transmittantur. Sed ad securitatem retis curandam, filtratio fasciculorum traditionalis longe a sufficientia est. Nonnullae ex praecipuis methodis inspectionis profundae fasciculorum in administratione retis infra enumerantur:
Modus/Subscriptio Congruens
Quisque fasciculus a muro ignis cum facultatibus systematis detectionis intrusionum (IDS) pro congruentia cum indice impetuum notorum in retibus examinatur. IDS exempla specifica noxia nota quaerit et commeatum inhibet cum exempla noxia inveniuntur. Incommodum consilii congruentiae signaturarum est quod solum ad signaturas quae frequenter renovantur pertinet. Praeterea, haec technologia solum contra minas vel impetus notos defendere potest.
Exceptio Protocoli
Cum ars exceptionis protocolli non simpliciter omnia data quae non congruunt cum indice subscriptionum permittat, ars exceptionis protocolli a muro ignis IDS adhibita vitia inherentia methodi comparationis exemplaris/subscriptionum non habet. Potius, politicam reiectionis implicitam adoptat. Per definitionem protocolli, muros ignis decernunt quae commeatus permitti debeat et rete a periculis ignotis protegunt.
Systema Praeventionis Intrusionis (IPS)
Solutiones IPS transmissionem fasciculorum noxiorum propter contenta impedire possunt, ita impetus suspectos in tempore reali prohibentes. Hoc significat, si fasciculus periculum securitatis notum repraesentat, IPS proactive negotiationem retiariam secundum regulas definitas obstruere. Unum incommodum IPS est necessitas regulariter renovandi basem datorum minarum cyberneticarum cum informationibus de novis minis et possibilitate falsorum positivorum. Sed hoc periculum mitigari potest creando rationes conservativas et limina propria, statuendo modum agendi fundamentalem aptum pro componentibus retiariis, et periodica aestimatione monitorum et eventuum relatorum ad augendam observationem et admonitionem.
1- DPI (Inspectio Profunda Fasciculorum) in Intermediario Fasciculorum Reticulari
"Profunda" est comparatio plani et analysis fasciculorum ordinariorum, "inspectio fasciculorum ordinaria" solum analysis sequens fasciculorum IP quattuor stratorum, inclusis inscriptione fontis, inscriptione destinationis, portu fontis, portu destinationis et genere protocolli, et DPI praeter analysin hierarchicam, etiam aucta analysis strati applicationis, varias applicationes et contenta identificans, ad functiones principales perficiendas:
1) Analysis Applicationis -- analysis compositionis negotiationis retialis, analysis effectus, et analysis fluxus
2) Analysis Usorum -- differentiatio gregis usorum, analysis habituum, analysis terminalium, analysis tendentiarum, etc.
3) Analysis Elementorum Reticuli -- analysis secundum attributa regionalia (urbem, regionem, viam, etc.) et onere stationis basis fundata.
4) Moderatio Trafficae -- limitatio celeritatis P2P, certitudo QoS, certitudo latitudinis nexus, optimizatio opum retiariarum, etc.
5) Securitas confirmata -- impetus DDoS, tempestas datorum divulgatarum, prohibitio impetuum virorum malitiosorum, etc.
2- Classificatio Generalis Applicationum Retialium
Hodie innumerabiles applicationes in Interreti exstant, sed applicationes interretiales communes exhaurientes esse possunt.
Quantum scio, optima societas recognitionis applicationum est Huawei, quae quattuor milia applicationum agnoscere profitetur. Analysis protocollorum est modulus fundamentalis multarum societatum muri ignis (Huawei, ZTE, etc.), et est etiam modulus magni momenti, adiuvans ad exsecutionem aliorum modulorum functionalium, accuratam identificationem applicationum, et magnopere emendans efficaciam et firmitatem productorum. In simulatione identificationis programmatum malignorum secundum proprietates negotiationis retialis, sicut nunc facio, accurata et ampla identificatio protocollorum etiam magni momenti est. Excluso negotiatione retiali applicationum communium a negotiatione exportationis societatis, negotiatio reliqua parvam partem repraesentabit, quae melior est ad analysin et admonitionem programmatum malignorum.
Ex mea experientia, applicationes vulgo adhibitae secundum functiones suas digeruntur:
PS: Secundum propriam intelligentiam classificationis applicationis, si quid boni suggestionis habes, libenter nuntium relinque.
1). Litterae electronicae
2). Video
3). Ludi
4). Classis Officii OA
5). Renovatio programmatis
6). Pecunia (banca, Alipay)
7). Actiones
8). Communicatio Socialis (programmatura nuntiationis instantaneae)
9). Navigatio interretialis (probabiliter melius cum URLs cognoscitur)
10). Instrumenta demptionis (discus interretialis, demptio P2P, ad BT pertinens)
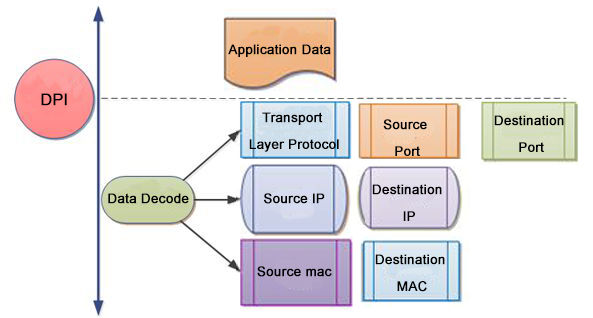
Deinde, quomodo DPI (Inspectio Profunda Fasciculorum) in NPB operatur:
1). Captura Fasciculorum: NPB negotiationem retiariam ex variis fontibus, ut commutatoribus, itineribus, vel receptaculis, capit. Fasciculos per rete fluentes accipit.
2). Analysis Fasciculorum: Fasciculi capti a NPB analizantur ad varia strata protocollorum et data conexa extrahenda. Hic processus analizationis adiuvat ad identificandas diversas partes intra fasciculos, ut capita Ethernet, capita IP, capita strati translationis (e.g., TCP vel UDP), et protocolla strati applicationis.
3). Analysis Oneris Utilis: Cum DPI, NPB ultra inspectionem capitis progreditur et in onus utile intendit, incluso ipso dato intra fasciculos. Contentum oneris utilis penitus examinat, nulla ratione applicationis vel protocolli adhibiti, ut informationes pertinentes extrahat.
4). Identificatio Protocollorum: DPI NPB sinit protocolla et applicationes specificas intra negotiationem retiariam adhibitas identificare. Protocolla sicut HTTP, FTP, SMTP, DNS, VoIP, vel protocolla diffusionis imaginum detegere et classificare potest.
5). Inspectio Contenti: DPI permittit NPB contenta fasciculorum inspicere ad exempla, signaturas, vel verba clavis specifica invenienda. Hoc permittit detectionem minarum retiariarum, ut programmata noxia, virus, conatus intrusionis, vel actiones suspectas. DPI etiam adhiberi potest ad contenta filtranda, normas retiarias exsequendas, vel violationes obsequii datorum identificandas.
6). Extractio Metadatarum: Per DPI, NPB metadata pertinentia ex fasciculis extrahit. Hae informationes sicut inscriptiones IP fontis et destinationis, numeri portuum, singula sessionum, data transactionum, vel alia attributa pertinentia includere possunt.
7). Directio vel Filtratio Traffici: Fundata in analysi DPI, NPB fasciculos specificos ad destinationes designatas ad ulteriorem processum dirigere potest, ut instrumenta securitatis, instrumenta monitoria, vel suggesta analytica. Etiam regulas filtrationis applicare potest ad fasciculos reiciendos vel rediregendos secundum contenta vel exempla identificata.
Tempus publicationis: XXV Iunii MMXXIII