TheIntermediarius Fasciculorum Reticularium(NPB), quod comprehendit vulgo adhibitas 1G NPB, 10G NPB, 25G NPB, 40G NPB, 100G NPB, 400G NPB, etPortus Accessus Probationis Retialis (TAP), est instrumentum hardware quod directe in funem retialem inseritur et partem communicationis retialis ad alia instrumenta mittit.
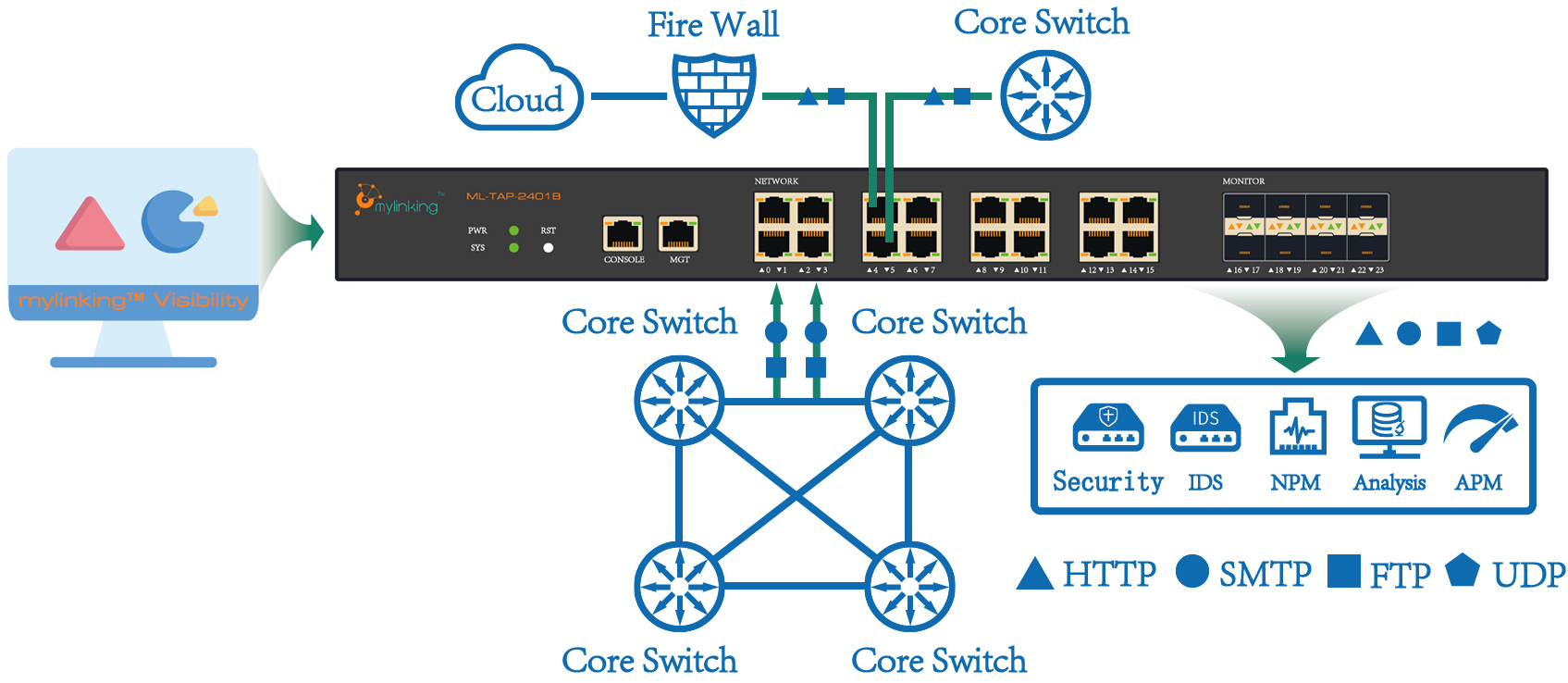
Intermediarii fasciculorum retialium (Network Packet Brokers) vulgo in systematibus detectionis intrusionis retialis (IDS), detectoribus retialibus, et profilatoribus adhibentur. Sessio specularis portuum. In modo derivationis, nexus UTP monitoratus (nexus non personatus) in duas partes dividitur per instrumentum derivationis TAP. Data derivativa cum interfacie collectionis connectuntur ad colligenda data pro systemate monitorio securitatis informationum interretialium.
Quid tibi praestat Network Packet Broker (NPB)?
Proprietates Claves:
1. Independens
Est pars apparati sui iuris nec onus instrumentorum retiariorum existentium afficit, quod magna commoda prae imagine portuum (port mirroring) habet.
Instrumentum in linea est, quod simpliciter significat id in reti coniungi debere. Attamen, hoc etiam incommodum habet quod punctum defectus inducit, et quia instrumentum in linea est, rete praesens tempore dispositionis interrumpi debet, pro loco ubi dispositum est.
2. Perspicuus
"Perspicuum" significat indicem ad rete praesens. Post accessum ad derivationem retialem, nullam vim in omnibus machinis in reti praesenti habet, et eis omnino perspicuum est. Scilicet, hoc etiam includit commeatum a derivatione retiali ad machinam monitoriam missum, quod etiam reti perspicuum est.
Principium operandi:
Distributio commeatus secundum data ingressa, replicationem, collectionem, filtrationem, transformationem datorum 10G POS per conversionem protocolli ad decem megabytes data LAN, secundum algorithmum specificum ad librationem oneris egressa, egressum simul ut omnes fasciculi eiusdem sessionis, vel eiusdem IP, omnes fasciculos ex eadem interfacie usoris emittant.
Proprietates Functionales:
1. Conversio protocolli
Interfacies communicationis datorum interretialis vulgares, quas ISP adhibent, 40G POS, 10G POS/WAN/LAN, 2.5G POS, et GE comprehendunt, dum interfaces receptionis datorum, quas servitores applicationum adhibent, interfaces GE et 10GE LAN sunt. Quapropter, conversio protocolli, quae in interfaciibus communicationis interretialis plerumque commemoratur, praecipue ad conversionem inter 40G POS, 10G POS, et 2.5G POS ad 10GE LAN vel GE refertur, et cotransferentiam bidirectionalem inter 10GE WAN et 10GE LAN et GE refertur.
2. Collectio et distributio datorum.
Plurimae applicationes collectionis datorum negotiationem quam curant extrahunt et negotiationem quam non curant reiiciunt. Commeatus datorum ab inscriptione IP specifica, protocollo, et portu extrahitur per convergentiam quintuplarum (inscriptione IP fontis, inscriptione IP destinationis, portu fontis, portu destinationis, et protocollo). Cum emittitur, eadem origo, eadem locus, et libratio oneris emissa secundum algorithmum HASH specificum praestant.
3. Filtratio codicis proprietatum
Ad collectionem commeatus P2P, systema applicationis fortasse tantum in quoddam commeatum specificum intendat, ut in mediis fluentibus PPStream, BT, Thunderbolt, et verbis clavibus communibus in HTTP ut GET et POST, etc. Methodus comparationis codicis proprietatum ad extractionem et convergentiam adhiberi potest. Derivator filtrationem codicis proprietatum in positione fixa et filtrationem codicis proprietatum fluitantis sustinet. Codex proprietatum fluitans est offset specificatum secundum codicem proprietatum in loco fixo. Idoneus est applicationibus quae codicem proprietatum filtrandum specificant, sed locum specificum codicis proprietatum non specificant.
4. Administratio sessionum
Frequentias sessionum identificat et valorem N transmissionis sessionis (N=1 ad 1024) flexibiliter configurat. Hoc est, prima fascicula N cuiusque sessionis extrahuntur et ad systema analysis applicationis posterioris transmittuntur, fasciculi autem post N abiciuntur, quo onus pro suggestu analysis applicationis posterioris conservatur. In genere, cum IDS ad eventa monitoranda uteris, non opus est omnes fasciculas totius sessionis tractare; potius, simpliciter prima fascicula N cuiusque sessionis extrahere debes ad analysin et monitorationem eventuum perficiendam.
5. Speculatio et replicatio datorum
Divisor potest imaginem et replicationem datorum in interfacie egredienti efficere, quod accessum ad data systematum applicationum plurium praestat.
6. Acquisitio et transmissio notitiarum retiaculi 3G
Collectio et distributio datorum in retibus 3G a modis traditionalibus analysis retium differunt. Fasciculi in retibus 3G per nexus principales per multiplices stratas encapsulationis transmittuntur. Longitudo fasciculorum et forma encapsulationis ab illis fasciculorum in retibus communibus differunt. Separator protocolla cuniculi, ut fasciculos GTP et GRE, fasciculos MPLS multistratos, et fasciculos VLAN, accurate identificare et tractare potest. Fasciculos signalationis IUPS, fasciculos signalationis GTP, et fasciculos Radius ad portus definitos secundum proprietates fasciculorum extrahere potest. Praeterea, fasciculos secundum inscriptionem IP internam dividere potest. Sustentatio fasciculorum nimis magni (MTU > 1522 Byte) tractandi, collectionem datorum retium 3G et applicationem derivationis perfecte perficere potest.
Requisita Proprietatum:
- Distributionem negotiationis per protocollum applicationis L2-L7 sustinet.
- Sustinet filtrationem quintuplarum secundum inscriptionem IP fontis exactam, inscriptionem IP destinationis, portum fontis, portum destinationis, et protocollum necnon cum larva.
- Aequationem oneris exitus et homologiam et homologiam exitus sustinet.
- Filtrationem et transmissionem per series characterum sustinet.
- Administrationem sessionum sustinet. Primos N fasciculos cuiusque sessionis transmittit. Valor N specificari potest.
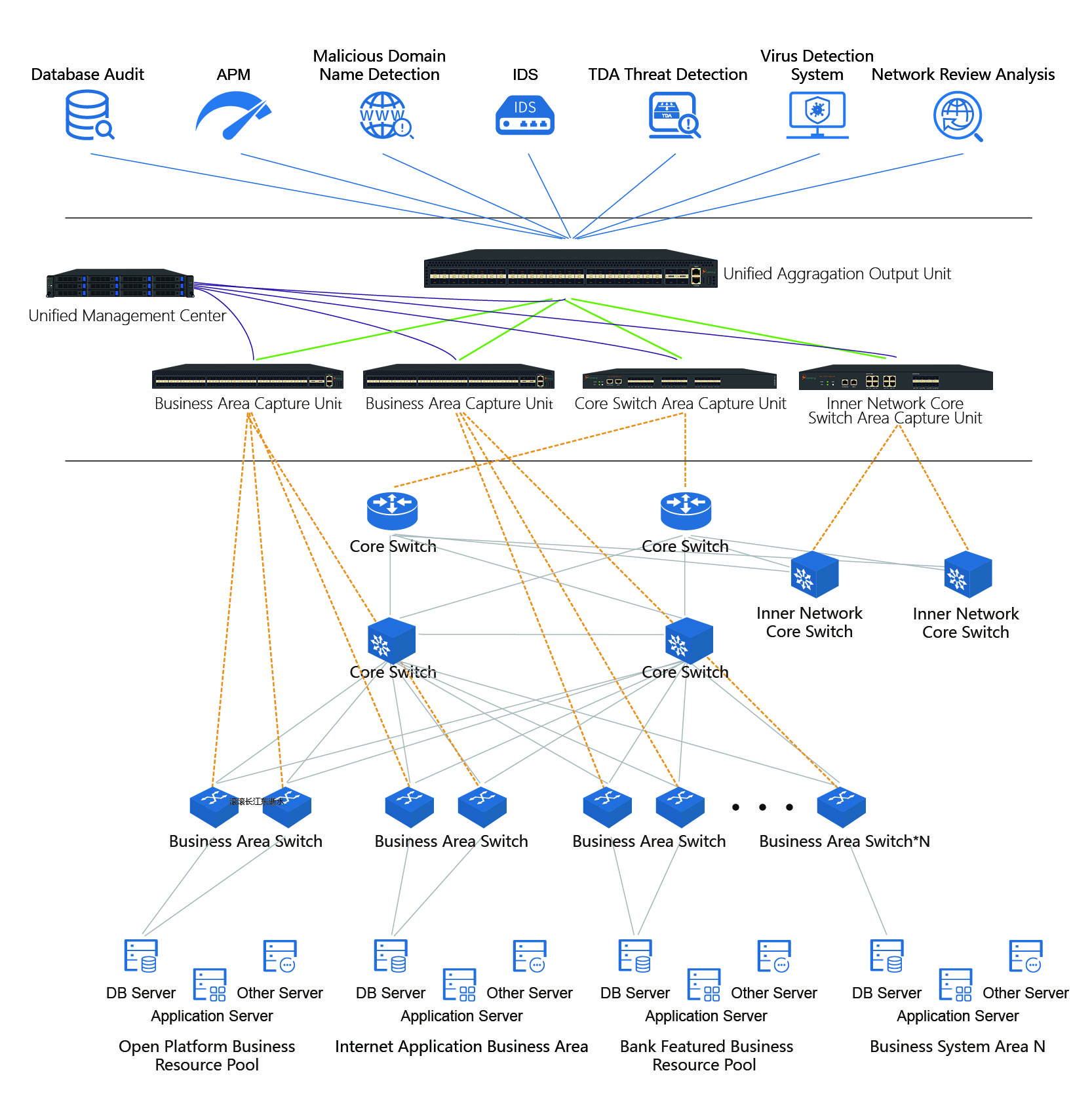
- Plures usores sustinet. Fasciculi datorum eidem regulae congruentes tertiae parti simul tradi possunt, vel data in interfacie emissa duplicari et replicari possunt, accessum ad data systematum applicationum plurium praebentes.
Solutio Industriae Pecuniariae Solutio Commoditatis Solutio
Cum celeriter technologiae informationis globalis progressae et informatizationis profundiore, magnitudo retium societatum paulatim amplificata est, et dependentia variarum industriarum a systematibus informationis magis magisque aucta est. Simul, impetus interni et externi, irregularitates, et minae securitatis informationis in reti societatum etiam crescunt, cum magna copia tutelae retium, systemata applicationum monitoriae negotialis deinceps in operationem inducantur, omne genus monitoriae negotialis, apparatus tutelae salutis per totam retem dispositi, dissipatio opum informationis, punctum caecum monitorium, monitorium repetitum, topologia retis et problemata inordinata, ut incapacitas efficaciter ad data destinata obtinenda, ducunt ad instrumenta monitoria parvam efficientiam operandi, magnam pecuniam collocatam, parvum reditum, tardam difficultatem conservationis et administrationis, et difficultatem ad opes datorum moderandas.
Tempus publicationis: VIII Septembris, MMXXII